Now that HTTPS and modern encryption has been worked-around for webOS, the next big challenge in repairing/maintaining apps is what Microsoft calls "Modern Auth."
Don't let the term fool you, its just OAuth2 -- which isn't that modern, and honestly not that secure. It replaces sending a username and password over the wire with a token: a long string of characters that's hard/difficult to brute-force and impossible to guess. If you can insert a man-in-the-middle, though, its still easily defeated. Some services work-around this constraint with shorter life tokens. Others just pretend its better. Still others just shut down their public API all-together in favor of their first party apps (which obviously will never come to webOS.)
As a result, some apps will never be repair-able (WhatsApp, for example) but those that were only out-of-reach due to "Modern Auth" might now be possible…
The biggest challenge with OAuth2 is that it involves redirection to a web page hosted by the authenticating service. Its not possible to write a webOS-friendly version of this web page because its not within the control of the app -- by design, the page is presented by the remote service. Of course we can't expect service providers to offer up a vintage-browser-friendly login page. The result is usually a blank frame, or some garbled UI that doesn't function.
However, a pattern exists for facilitating login for HTML-challenged screens. Netflix does it on smart TVs and streaming boxes: a unique code is generated that represents the device, you enter that code on a PC or Mac (or smart phone), complete the remote login on behalf-of the TV, then the TV gets the token. Why shouldn't this pattern be exploited for retro devices?!
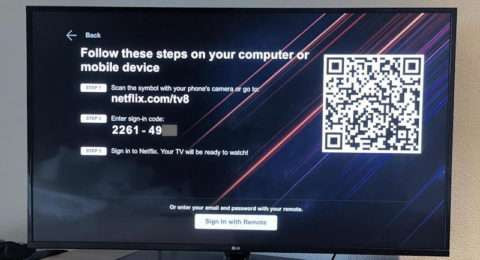
So that's what I did. The best explanation I've ever seen of OAuth2 is on the Pocket developer page. I'm not sure how popular Pocket is (I've personally avoided it), but Firefox has integrated with them, and that's my browser of choice, so I decided to try it out. The result is the restored ReadOnTouch Pro app for webOS, which I've retrofit to follow the Netflix pattern of facilitated-OAuth2:
The code uniquely identifies your device/log-in attempt, the modern device interacts with the remote login service, the web service stores the token temporarily, the "Verify" button in the app fetches that token then stores it as a "password" for future API calls.
This pattern is entirely re-usable for other "Modern Auth" APIs, and opens the door to restoring other apps in the future. The code for the back-end is here: https://github.com/webOSArchive/pocket-auth
As always, forks, PRs and comments welcome!